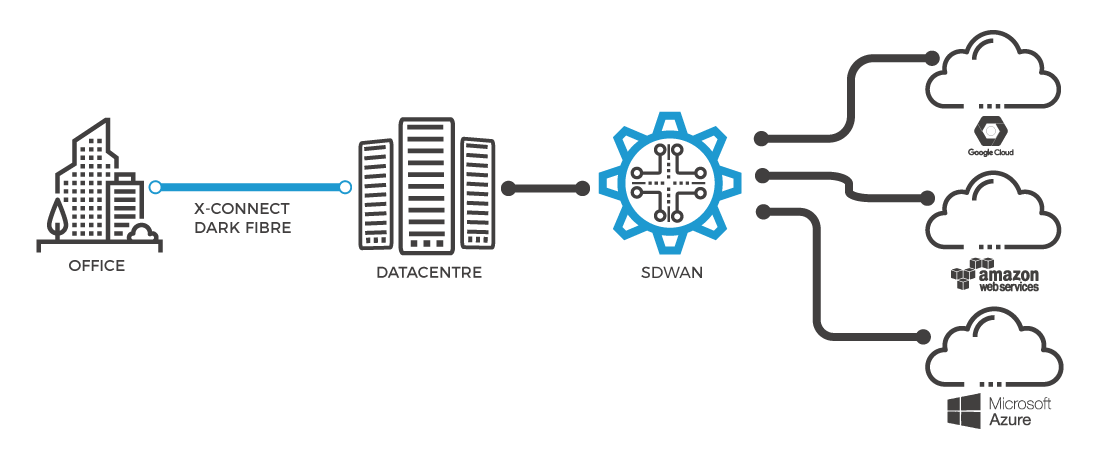
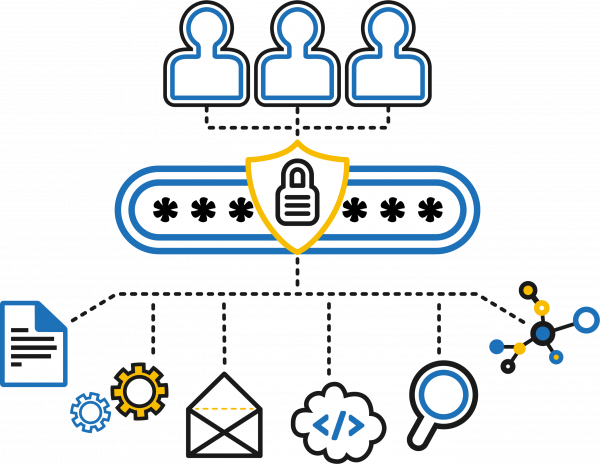
Novel Technologies stands at the forefront of cyber security, blending innovative approaches with industry-leading expertise to safeguard digital landscapes. Their proficiency spans a broad spectrum of services, from threat detection and prevention to comprehensive risk assessments and compliance strategies. Leveraging cutting-edge technologies and a highly skilled team, they deliver tailored solutions that anticipate and neutralize potential threats. Through continuous research and development, Novel Technologies ensures that their clients are always one step ahead in the ever-evolving world of cyber threats, embodying a commitment to excellence and security that sets them apart in the industry.

Endpoint Protection
Endpoint protection is a type of cybersecurity solution that focuses on protecting endpoints, such as laptops, desktops, mobile devices, and servers, from cyber threats. Endpoint protection solutions typically include antivirus, anti-malware, and anti-spyware software, as well as firewalls and intrusion prevention systems.